First of all, I would like to thank everyone who made this possible: the Objective-See Foundation, the organizers, the trainers, speakers, sponsors, and all the attendees who made the week so welcoming.
But most importantly: thank you to Andy Rozenberg and Patrick Wardle for selecting me for a full scholarship to attend Objective by the Sea (OBTS) v8.0. It covered my flight, hotel, training and conference ticket. This is one of those things you dream about when you’re a random student… and then it actually happens.
What’s OBTS v8.0?#
Objective by the Sea (OBTS) is one of the must-attend conferences for Apple platform security (macOS, iOS, watchOS, etc.).
OBTS v8.0 took place in Ibiza (Spain) in October 2025, with:
- 3 days of training (October 12th → 14th)
- 3 days of talks (October 15th → 17th)
- plus community events… including an Apple-themed CTF
The conference is organized by the Objective-See Foundation, a non-profit that creates free macOS security tools, supports the community, and runs programs like Objective-We (mentorship, training, scholarships, conference opportunities, etc.).
If you are into Apple security, OBTS is one of the rare places where the “esoteric” becomes very concrete: you learn, you meet people doing this for real (research, IR, forensics, red team, product security…), and you come back home with a bigger to-do list.

Why I applied for a scholarship#
A few months before OBTS, I attended OFTW v3.0 in London (also organized by the Objective-See Foundation). I wrote a full debrief here:
At OFTW I met Andy & Patrick, and Andy encouraged me to apply for the OBTS scholarship. So I did.
I’m currently a French cybersecurity student (Master’s degree) at École 2600 and I’ve spent the last few years learning about forensic, IR, reverse and a bit later on, Apple security, especially iOS. I also do a lot of CTF solo and with my school team Phreaks2600.
This scholarship was more than “just” financial support. It felt like:
- someone believes you can contribute to this community
- someone wants you in the room
- someone wants to lower the barrier of entry for people who are motivated but not always funded
And honestly, that’s cool.
Trainings (my pick)#
At OBTS v8.0, I attended:
iOS Threat Hunting & Malware Analysis#

This training by Matthias Frielingsdorf was exactly what I was looking for.
Why it clicked with me (personal + studies):
- It connected perfectly with my current interests: iOS internals and forensics on cool stuff like spyware etc.
- It helped me structure things I had learned “piece by piece” into a clearer mental model: what to collect, what to look for, how to reason about artifacts, and what “good” looks like when you do mobile triage / threat hunting.
One of my favorite parts was simply being able to ask questions and have direct feedback.
Talks#
The talk lineup was stacked. Instead of trying to summarize everything, here are a few talks that I personally loved and that I recommend watching / reading about (everything is available on OBTS Youtube channel or website):
- Make XNU
GREATLittle Again - Jonathan Levin - Unpacking the iOS Sandbox - Yarden Hamami
- Something from Nothing - Exploiting Memory Zeroing in XNU - Ian Beer
- Breaking the Sound Barrier: Exploiting CoreAudio via Mach Message Fuzzing - Dillon Franke
- What’s new in Lockdown Mode? - Marie Fischer
- Crash One - A StarBucks Story (CVE-2025-24277) - Csaba Fitzl & Gergely Kalman
- Placeboed Apples: A New Way to Hunt Spyware on iOS - Matthias Frielingsdorf
- Reverse Engineering Apple Security Updates - John McIntosh
- Dylib Hijacking on macOS: Dead or Alive? - Patrick Wardle
The OBTS CTF#
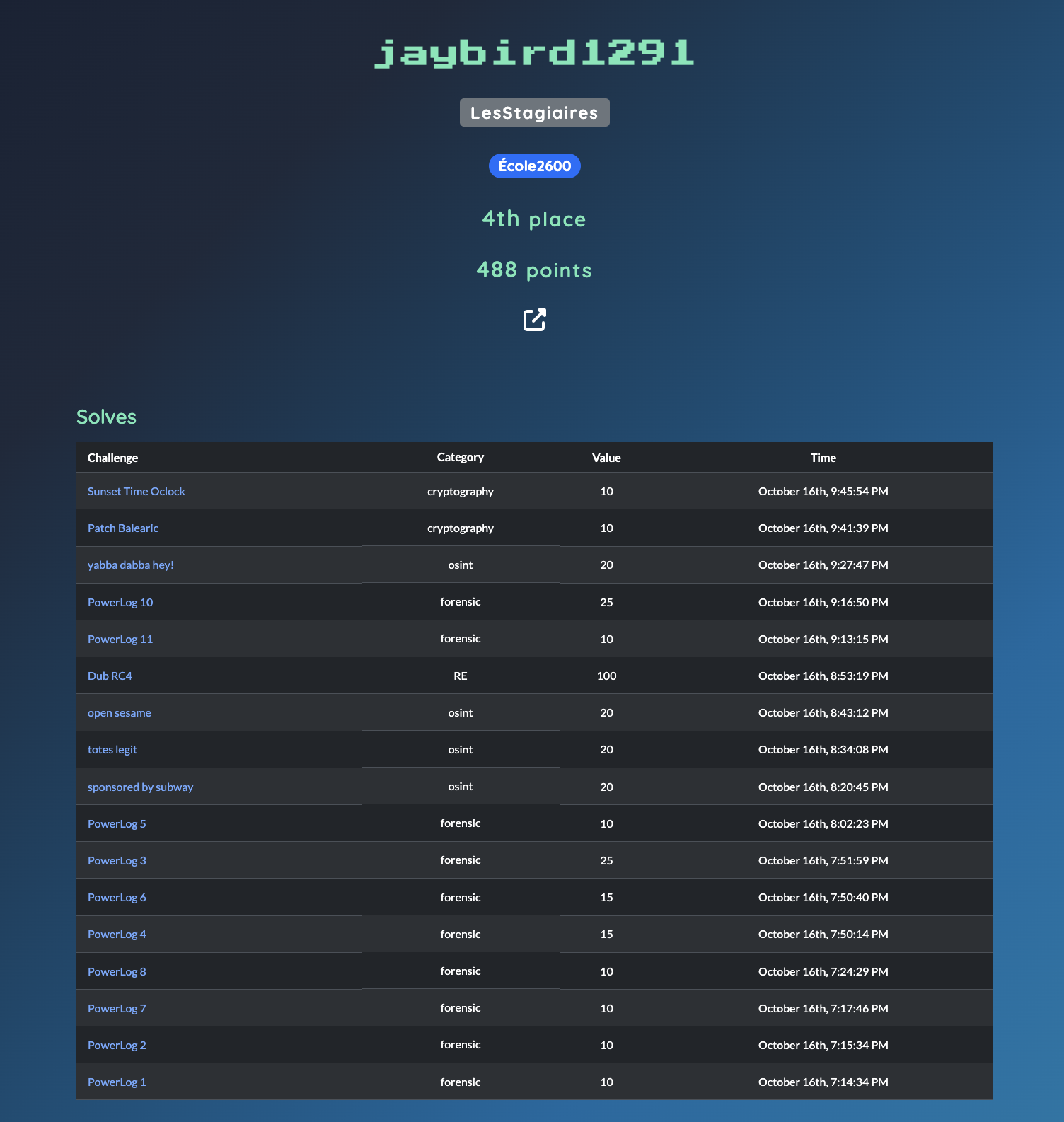
There was a CTF during the conference which was pretty cool!
This one was Apple-themed, with challenges that really fit the spirit of the event.
I wrote some writeups so don’t hesitate to check this out: https://jaybird1291.github.io/blog-cyber/posts/obts-v8/
Community / networking#
Technical content is amazing, but OBTS is also about the people.
I had conversations with:
- students who are grinding just like me,
- really cool and interesting researchers,
- people working in incident response / threat intel / product security,
- and people who have been in Apple security for a long time (and are still humble and easily approachable).
Being in that environment makes you raise your own standards.
About the scholarship#

What I put forward in my application was:
- A clear technical focus (Apple platform security, especially iOS) and why it matters to me.
- Proof of work: blog posts, writeups, CTF practice, and the fact that I keep learning in public (even when it’s messy).
- Relevant experience (what I’ve done in internships etc., what I’ve learned from classes, CTF etc.).
- A concrete reason OBTS was the right place (specific trainings/talks that matched my interests, and what I hoped to learn).
- What I would do with the opportunity afterward: keep publishing, keep practicing, and convert the week into output rather than letting it fade.
Also: I tried to make it easy for the reviewers to understand my trajectory in two minutes. If you apply, keep it simple: show that you’re serious, that you’ve already started the journey, and that the scholarship will actually amplify momentum that already exists.
Most importantly: ask. Be polite, be honest about your constraints, and show that you’re ready to work. Even if you don’t get it, you lose nothing and sometimes you get what you wanted.
Don’t hold back, apply, ask, try#
If there is one message I want to leave here:
Never self-reject.
Don’t assume you’re “not good enough” to apply to a scholarship, a conference, a training, a job, a mentorship program, a CTF team, etc.
- Apply.
- Ask.
- Show up.
- Work.
- Try (even if you fail).
Even when you don’t get what you want the first time, you still get something: experience, feedback, connections, and momentum. And over time, that gets rewarded.
So if OBTS / OFTW / anything like this is on your radar: go for it.
How to get the most out of OBTS#
Such a conference can be overwhelming, especially as a student, in the best possible way: advanced content, a lot of strong profiles, and a week that goes by fast. If you’re coming as a student a few simple habits make a massive difference:
Prepare your “professional surface area.”
Refresh your LinkedIn, make sure you have a clean way to share your work (a blog, GitHub etc.), and publish a couple of notes/writeups you’re comfortable standing behind. Also, have a dedicated contact channel ready (a professional email address, a Discord handle you actually monitor, etc.). You may meet people who will matter in your career sooner than you think.Do a small “pre-OBTS warm-up” the week before.
Skim past OBTS/OFTW talks & slides, refresh the basics you know you’ll need (macOS internals, iOS architecture, reversing fundamentals, common security primitives).Set a goal that’s realistic and measurable.
Mine was: (1) learn more about iOS security, (2) leave with a concrete resources list (talks, articles, blog posts, trainings etc.), and (3) meet people I can learn from. A clear target prevents you from trying to absorb everything and retaining nothing.Treat trainings like a lab, not like a lecture.
Take notes in a way you can reuse later: commands, decision points, “if X then Y” logic, and pitfalls. After each day, rewrite the messy notes into a short checklist while it’s still fresh.Ask questions early, even if they feel “basic”.
The gap between “I kind of get it” and “I can apply it” is usually one good question.Use the hallway track intentionally.
Pick 2–3 topics you genuinely care about (iOS security, forensics / malware / threat hunting) and start conversations around those. It’s easier than trying to “network” in the abstract, and you’ll meet the right people naturally.Follow up after the conference.
Send a short message to people you met (“thanks for the chat about X, here’s what I’m reading/trying next”). If you publish a writeup/debrief, share it. This is how a single week becomes a long-term acceleration.
If you’re hesitating because you think you’re “not advanced enough” that feeling is normal. I felt it too, and I guess most people do. But after receiving scholarships for OFTW v3 and OBTS v8 etc., I realized something simple: most people in this community are genuinely approachable and truly want to help. Don’t be afraid, try and see.
Resources#
Official links:
- OBTS v8.0: https://objectivebythesea.org/v8/index.html
- OBTS v8.0 schedule: https://objectivebythesea.org/v8/schedule.html
- Objective-See Foundation: https://objective-see.org/
- Objective-We (scholarships, trainings, mentorship): https://objective-see.org/we.html
- Objective-See “Steve” (helps candidates & company to meetup) : https://objective-see.org/steve.html
Other write-ups / references (worth reading):
- RandoriSec OBTS 2025 recap: https://blog.randorisec.fr/conference-obts-2025/
- CTFIOT overview (Chinese): https://www.ctfiot.com/274796.html